
SECURED DEVICE SERVICES
Secured Device Services (SDS) is dedicated to creating a secure and efficient computing environment for our campus community.
By providing comprehensive device administration and security services, we ensure that your technology remains protected and up-to-date. Timely patches and critical operating system updates safeguard your devices from the latest cybersecurity threats while minimizing the need for user maintenance.
SDS covers a wide range of devices, from desktops and laptops to smartphones and tablets, offering peace of mind and allowing you to focus on your work.
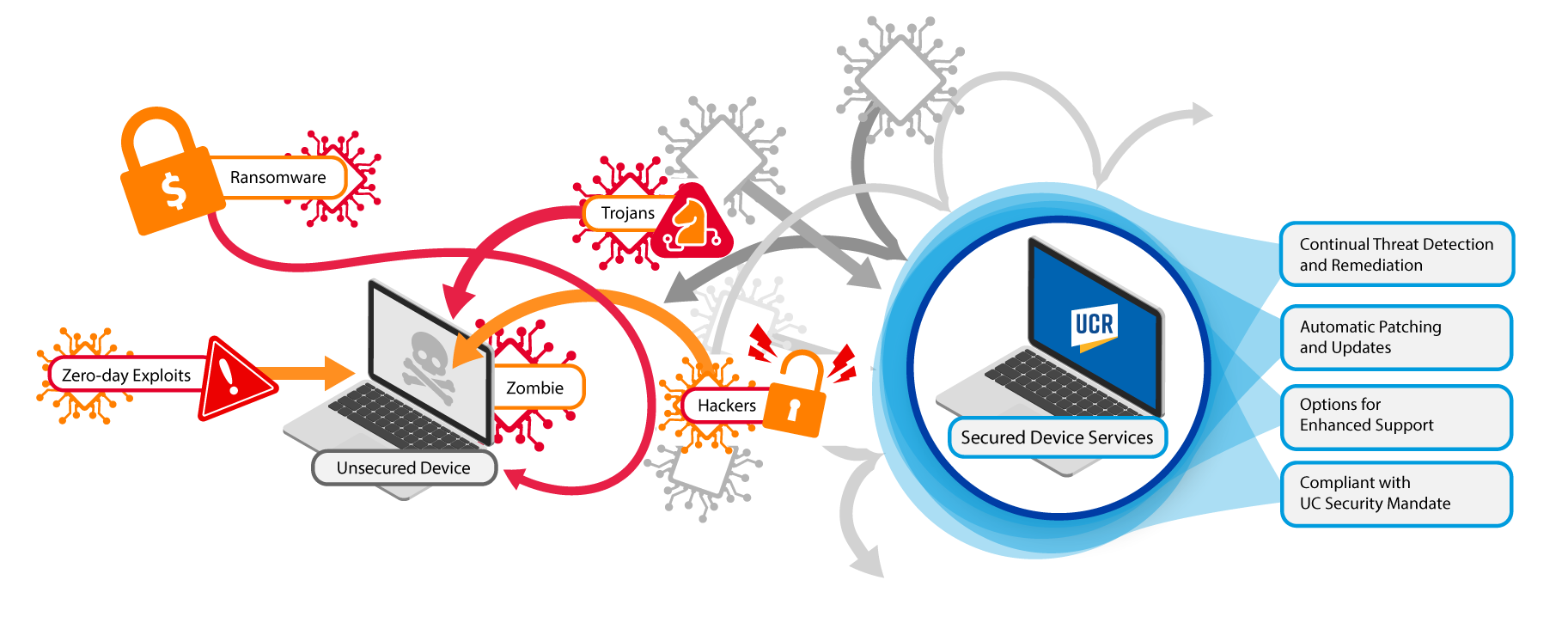

BENEFITS OF SDS

Enhanced Security
↓
Experience a fortified end-user environment, safeguarding your data and sensitive information.

Streamlined Administration
↓
Let us handle the complexities of device management, freeing your time for more important tasks.
Note: Through SDS, Departments are still responsible for the purchase of devices and asset management. View recommended device standards and asset management best practices to get your department setup for success. SDS members can leverage the campus instance of Asset Panda for IT asset management.

Accessible Technology
↓
Get the devices you need, ensuring you have the tools to succeed.

Simplified Application Management
↓
Access the software you require seamlessly, with updates and installations managed behind the scenes.*
*Note: While a majority of installs can be done remotely, some installations may require in-person assistance, especially for customized software.

Consistent User Experience
↓
Enjoy a uniform and reliable computing experience across all your devices in your department.

USER TYPES
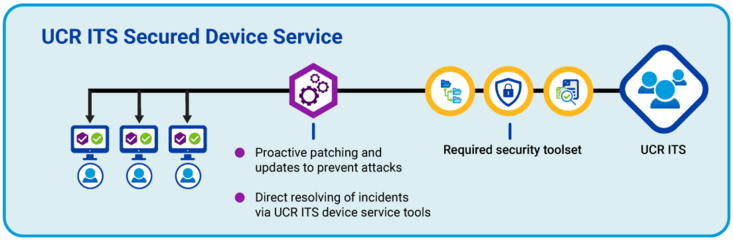
ITS Secured Device Service Users
Who are ITS Secured Device Service Users?
ITS Secured Device Service Users are departments or groups who have a current agreement with ITS to manage, update, repair, and maintain their devices.
What steps must ITS Secured Device Service Users take to comply with the UC cybersecurity mandate 2025?
Current SDS Users do not need to take any action at this time. As some users may be part of the legacy Managed Desktop program, they may need to have the newer security tools installed as part of this effort. ITS is currently performing a physical inventory of these departments and devices to ensure that they are protected with the latest security tools. ITS will be contacting all ITS Secured Device Service Users to coordinate.
Often, security concerns may be addressed with replacement of aging equipment. ITS has created and published hardware and device standards for equipment that meets the majority of enterprise standards and encourages departments to utilize these standards, as well as UCR’s contracted pricing, when purchasing new equipment.
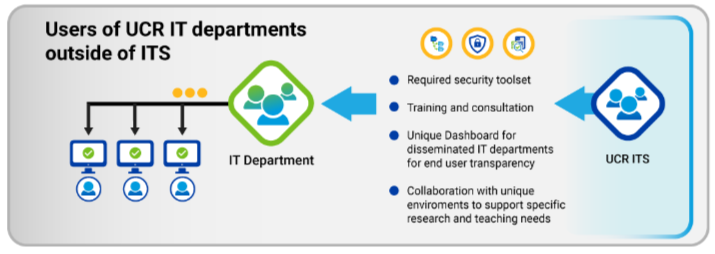
Users of UCR IT departments outside of ITS
Who are Users of UCR IT departments outside of ITS?
Users of UCR IT departments outside of ITS are departments or groups who have their own, internal IT staff, responsible for the security, maintenance, and repair of devices. While these groups may collaborate with ITS, generally they have a distinct environment, and potentially their own domain.
What steps must Users of UCR IT departments outside of ITS take to comply with the UC cybersecurity mandate 2025?
A designated representative from the department’s IT staff will need to coordinate with ITS to secure the tools, software, and training needed to bring their departments into compliance.
Often, security concerns may be addressed with replacement of aging equipment. ITS has created and published hardware and device standards for equipment that meets the majority of enterprise standards and encourages departments to utilize these standards, as well as UCR’s contracted pricing, when purchasing new equipment.
Self-Maintained Device Users
Who are Self-Maintained Device Users?
Self-Maintained device users are individuals who are not managed by ITS and do not have dedicated IT staff to coordinate this effort. These individuals may have devices purchased with grant money or other non standard funds, but will still need to meet the security requirements.
What steps must Self-Maintained Device Users take to comply with the UC cybersecurity mandate 2025?
Self-maintained users will need to coordinate with ITS to install the software needed to bring their devices into compliance.
Often, security concerns may be addressed with replacement of aging equipment. ITS has created and published hardware and device standards for equipment that meets the majority of enterprise standards and encourages departments to utilize these standards, as well as UCR’s contracted pricing, when purchasing new equipment.

Am I currently a part of Secured Device Services?
Check to see if you are a member of Secured Device Services.

FREQUENTLY ASKED QUESTIONS
-
How does SDS work?
SDS is a program that provides comprehensive device administration and security services to enrolled users. Departments may enroll in SDS to ensure that their technology remains protected and up-to-date. Interested departments may request a consultation.
Once enrolled, departments must provide their university issued devices to ITS for device administration setup. This process typically takes between 30 minutes to an hour. Once set-up is complete, the SDS toolset will actively safeguard your device from cyber threats.
-
Is there a cost associated with SDS?
Yes, there is a cost associated with SDS. The cost of SDS varies based on service level.
For more information related to program pricing, please contact ITS.
-
Which devices can be included in SDS?
Desktop and laptop computers, both Apple and Windows devices, as well as tablets and even phones can be secured through SDS. Please note, SDS does not purchase devices for those participating in the program, but can make recommendations based on campus standards. In conjunction with IT Asset Management (ITAM), SDS tests the latest standard devices to ensure that there are no concerns with equipment or compatibility.
Occasionally, SDS is asked to include devices that are outside of campus standards. This can be done but these devices are evaluated on a case by case basis in order to determine any conflicts with the security tools.
-
Can I join as a single user, or does my department need to join?
SDS is not taking single users at this time. SDS is most effective when entire departments join together.
Single users can download the security toolset mandated by the UC cybersecurity mandate 2025 without enrolling in SDS.
-
How do I download and install software on a SDS device?
SDS provides installers for the most common productivity software used on campus to participating departments for easy download and installation. Please note, software such as Microsoft desktop applications and Adobe may require additional licensing based on your department's contract.
Additional software can be installed with the help of a BearHelp technician via a support request.
Note: All software installed on campus devices goes through a vulnerability assessment and approval with the Information Security Office. If the software you are requesting has not yet been approved by the Information Security Office (ISO), there may be additional processes required prior to installation to ensure that the software does not present a vulnerability risk to campus.
-
What causes information security vulnerabilities within organizations?
Vulnerabilities are more commonly found on devices that have old, unsupported hardware which no longer receive new security updates. In addition, those that are on outdated Windows versions that are no longer eligible for the latest security updates are more susceptible to information security vulnerabilities.
SDS works to prevent information security vulnerabilities within UCR by ensuring the latest security updates are deployed to your department’s devices.
-
What are the risks involved when cybersecurity is weak?
Compliance with UC’s standard cybersecurity measures is essential to mitigate the risks of falling victim to cybercrime acts such as phishing, identity theft, and hacking, which can impede the University’s operations, divert funds, and damage our reputation. Joining SDS fortifies your department’s device security and maintains compliance with UC standards.
-
How does SDS ensure that I am compliant with the UC cybersecurity mandate 2025?
The UC cybersecurity mandate 2025 imposed by the UC President at the direction of the UC Regents requires that all UC locations must comply with new information security requirements. As a result, security tools must be installed on every university laptop and desktop to enable vulnerability monitoring and remediation, virus protection, and asset management.
SDS ensures that your department meets compliance by having the necessary cybersecurity tools downloaded. The current toolset for UC Riverside includes vulnerability management, detection, and response (VMDR), endpoint management (EM), and endpoint detection and response (EDR). The specific software programs delivering VDMR, EM, and EDR functionality to campus are constantly being evaluated for performance, impact, and features, and may be replaced with different software with similar or better functionality in the future.
-
What is the difference between managed and non-managed devices?
Managed devices refer to devices (e.g., desktops, laptops, smartphones, and tablets) that are managed, secured, and maintained either by ITS (including Secured Device Services) or by local UCR IT departments. Non-managed devices are managed and maintained by individuals with no administrative support from IT.
-
Are UCR employees required to use SDS?
As part of UCR's security investment roadmap, the Chancellor and Provost have called on all units to move to SDS to improve the university's security posture. While units are not expected to move before the May 28, 2025, UC Cybersecurity Mandate deadline, it is required that the UCR Security Toolset be installed on any device that is being used to perform university work.
